CVE-2019–1388: Windows Certificate Dialog Elevation of Privilege
Overview:
CVE-2019-1388 is a privilege escalation vulnerability seen within older implementations of Windows 7, 8, 10, and Server. It is a low complexity vulnerability, meaning exploitation is relativity simple/low level. It is not complex to take advantage of and does not require any ‘deep diving’ into the system. As a privilege escalation vulnerability it allows a standard low level user to escalate their privileges to that of an administrator which would allow free reign over the target machine. In terms of requirements to exploit, it really only requires an older signed Microsoft executable as well as a suitable target running the vulnerable version of Windows. Signed is important since we will be taking advantage of the certificate dialog. I used an executable specifically designed for this which you can find the link to further down. All that is needed is to place the executable onto the target and escalation can begin.
Lab Setup:
Setting up the lab is fairly simple. You will need your host/attacking machine, a vulnerable Windows virtual machine, and the executable to use. In my case, my attacking machine was a Kali Linux virtual machine. The target machine is running Windows 7 Ultimate with Service Pack 1 installed. There are other vulnerable versions of Windows you can use as well, I just chose to use Windows 7 in this case. For a reference of all the vulnerable versions of Windows for this CVE, refer to this screen capture taken directly from cvedetails.com:

Other than these requirements that's really all there is needed to set up this lab environment. Once the virtual machines are up and running and our executable is downloaded we will be set to go. No other downloads or extras are needed for this. I will provide links to all of the resources needed. Note that Windows 7 ISO files can be a bit of a pain to obtain if not directly from Microsoft (which requires a product key). I might recommend trying out the Windows 10 or Server implementations as obtaining the ISO files for those are much easier. I had to do a bit of searching to find a legitimate and safe download for a Windows 7 ISO file.
Kali Linux — https://www.kali.org/
Windows 7 Ultimate — https://www.softlay.com/operating-system/windows-7-ultimate-iso-download.html
hhupd.exe — https://packetstormsecurity.com/files/14437/hhupd.exe.html
Walk through:
- First, get the virtual machines downloaded and up and running. For my hypervisor I am using VirtualBox. Within the Windows machine I’d recommend enabling a guest account (which has the least amount of privileges) and logging in as that just so we can see the full force of this exploit. Once booted up and logged into the Windows machine, open up a command prompt and enter whoami to ensure you're logged in as a low level user. We can see below that I am a guest user on John’s PC.

2. Next we’re going to need to download our executable (hhupd.exe) onto our attacking machine. No need to run it. Within my Linux machine, I have it sitting right in my Downloads directory.
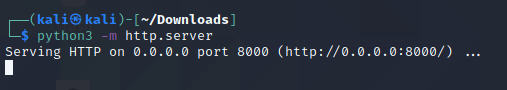
3. Now we’re going to transfer this executable onto the target machine. Methods may vary here depending on the OS of your attacking machine and how you want to transfer it. In my case I ran a simple Python HTTP server within the terminal and on the target machine, I opened a web browser and navigated to the web page to download the executable. hhupd.exe now lives on the Desktop of my Windows 7 target machine. If using the Python HTTP server, ensure you are within the directory where the executable lives before issuing the command.
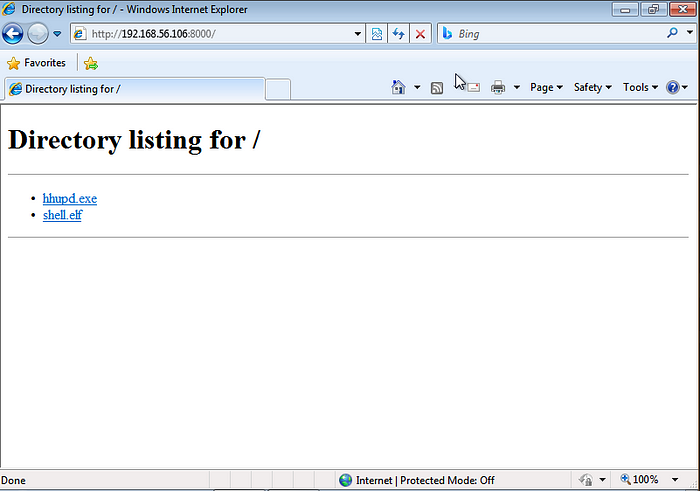
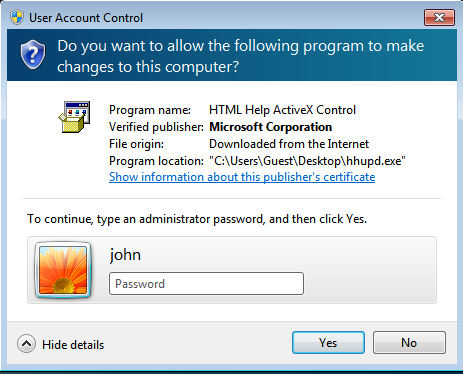
4. All the right strings are now in place and it is now time to begin the escalation phase. Navigate over to the newly transferred executable, right click on it, and click Run as administrator. A Windows User Account Control (UAC) window will pop up and prompt for an administrator password. There will be a highlighted link that says Show information about this publishers certificate. Click on that and you will be taken to another window that displays certificate information for the particular executable. The Issued By: line will display a highlighted hyperlink: Verisign Commercial Software Publishers CA which you can click on and then exit the open windows.
5. A web browser should automatically be opened from clicking on the hyperlink. If no web browser opens repeat step 4 until it does. Try clicking on the link multiple times before exiting the windows. In my case, the webpage didn’t actually fully load so if that happens to you it is no worry, just verify within the address bar that it has a Verisign address. Refer to the below image for verification:
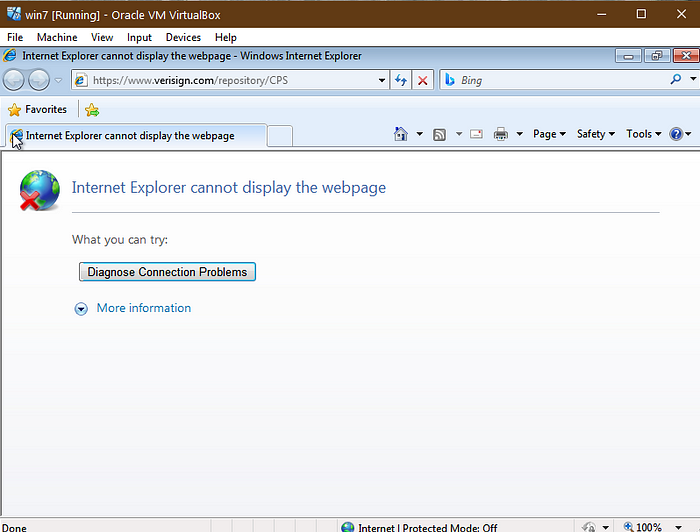
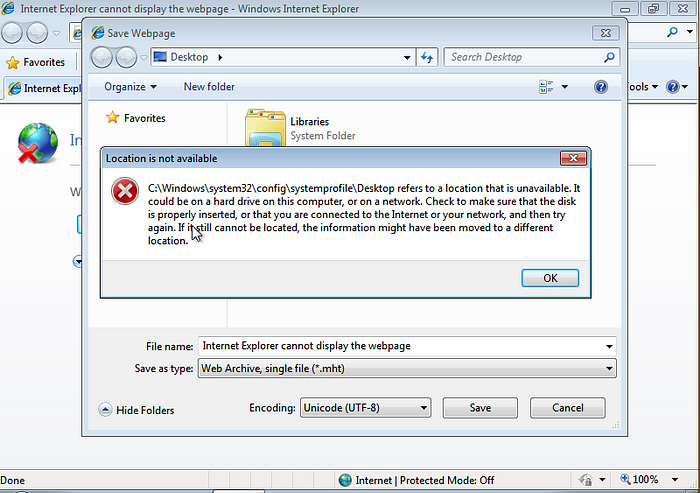
6. You will now go and save the webpage. This will vary on how it’s done depending on the browser but since I’m using Windows 7, the default browser is Internet Explorer. When attempting to save the webpage you will get a pop up that states Location is not available. This verifies that escalation is working good. Simply hit OK and proceed on. You will not actually save the webpage. Within file explorer, you will navigate to the C:\Windows\System32 directory. The quickest way to do this is within the File name bar, enter C:\Windows\System32\*.* This will take you right into the directory and list all of the contents of the System32 directory.

7. Within the System32 directory navigate down until you find the cmd executable. Right click on it and hit Open. A command prompt should open and to verify, type whoami and hit enter. whoami should display the current user as nt authority\system. This is much different than earlier when we entered whoami and it displayed as john-pc\guest. While logged in as a guest user we have opened a command prompt as NT Authority, which is the local account for most Windows services. NT Authority itself is the most powerful/one of the most powerful accounts on a Windows system and has access to all local system resources. We went from being the least privileged user in the beginning to the most powerful user, all without authentication. As an attacker we would have full reign over the target machine and could perform any task we’d like. Hopefully you can understand just how critical of a flaw and just how dangerous this really is. At this point we’ve done what's needed to be done. Our privileges have been escalated further than what they were before.
Remediation:
A full patch for this vulnerability was released in November of 2019 from Microsoft. Many implementations of Windows are vulnerable to this exploit and thus updating your operating system with all of the latest patches and security updates is crucial. If you happen to be running a vulnerable version of Windows, be sure to update as soon as you can before someone takes advantage of this against you or your company. Privilege escalation is dangerous. You have seen just how quickly and easily this can be exploited.
Conclusion:
In conclusion, exploiting CVE-2019–1388 allowed us to go from a guest user with limited privileges to a service account with full administrative privileges. Although not a particularly difficult exploit to walk through, it is quite dangerous in nature. The National Vulnerability Database, courtesy of NIST lists this CVE as a 7.8 and marked as “High” in severity. Given the privileges that can be escalated, I can see why they have this marked fairly high. I am hoping that by walking through this vulnerability, readers can learn more about the potential vectors that can be taken advantage of to exploit a system. I’ve seen lots of more complicated vulnerabilities with vast steps taken to exploit them, however something simple in comparison yet equally damaging still boggles my mind.